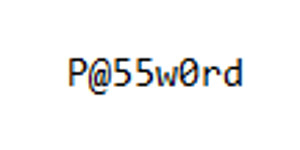As the digital landscape evolves, so does the sophistication of cyber threats, especially during peak times like the holiday season when e-commerce activity surges. One of the most common yet underestimated threats is weak passwords, which can serve as easy gateways for hackers into your WordPress site.
The Challenge of Creating Strong Passwords
Creating a new password is often a frustrating barrier to accessing new services, such as music streaming platforms. You’re eager to explore a new service, yet you’re stuck attempting to meet complex password requirements that leave you adding random numbers and symbols to your usual password. This not only heightens frustration but often results in a password you can’t remember later.
This scenario highlights a significant issue: many people’s passwords are simply too weak, making their personal and business accounts vulnerable to attacks.
Understanding Password Strength
What constitutes a strong password has evolved. In the early days of the internet, simple passwords might have sufficed. Today, however, cybercriminals use advanced tools that can quickly decode passwords through brute force attacks or by using sophisticated dictionaries that predict common password combinations like “P@55w0rd!”
To genuinely protect your accounts, especially your WordPress site, your passwords must be both long and random, making them harder for password-cracking tools to guess.
Modern Password Security Practices
As computing power increases, the ability of hackers to crack passwords grows. If your password includes common personal information, such as pet names or significant dates, it can be easily compromised. A robust password should be a random string of characters, which can be generated through tools like https://passwordsgenerator.net/ or the WordPress password creation tool, ensuring you avoid common biases and patterns.
Effective Methods to Manage Complex Passwords
The complexity needed for secure passwords makes them difficult to remember. While reusing passwords across multiple sites is risky, solutions like LastPass can help manage them by storing them securely. However, these systems are not infallible, as demonstrated by past breaches.
An increasingly recommended approach is to shift towards biometric and two-factor authentication (2FA) systems. These methods provide a higher level of security by requiring something you have (like a smartphone) or something you are (like a fingerprint), significantly enhancing your WordPress site’s security.
The Future of Password Security
With the relentless advancement of technology, the traditional password may soon be obsolete, replaced by more secure and user-friendly authentication methods. For many, the end of the password era cannot come soon enough, especially for those managing multiple accounts and seeking to secure their WordPress environments from increasingly sophisticated cyber threats.
In the meantime, strengthening your password practices is essential. For WordPress users, implementing advanced security measures can protect both your content and user data from potential breaches. If you’re looking to enhance your WordPress security, consider consulting with security experts who can provide tailored advice and solutions.
If you need guidance on securing your WordPress site or managing your digital security strategy, contact us at Watermelon Web Works for expert assistance.